搜索到
2
篇与
的结果
-
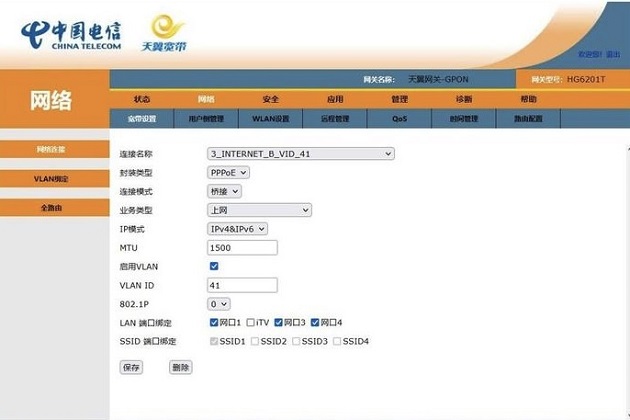
 Mikrotik RouterOS IPv6/IPv4双栈配置 前言IPv6:IPV6的提出最初是因为随着互联网的迅速发展,IPv4定义的有限地址空间将被耗尽,而地址空间的不足必将妨碍互联网的进一步发展。为了扩大地址空间,拟通过IPv6以重新定义地址空间。IPv6采用128位地址长度,几乎可以不受限制地提供地址。IPv4:IP协议的第4版本,IPV4为因特网上现行的最重要最基本的协议。IPv4采用32位地址长度,只有大约43亿个地址,目前已经面临分配枯竭。双栈(Dual-stack):双栈技术IPv4和IPv6共存运行在同一个网络一、准备工作RouterOS(ROS)是支持IPv6和IPv4双栈协议的配置的软路由系统。要想配置IPv4和IPv6双栈主要准备工作还是要当地ISP运行商支持。目前三大运营商都已经全部部署了IPv6,所有如果没有IPv6的小伙伴们可以咨询运行商提供。二、光猫IPv6/IPv4双栈配置为了实现RouterOS(ROS)是支持IPv6和IPv4双栈拨号,首先要在光猫上配置IPv6\IPv4双栈设置,当然前提是有光猫的超密才能修改,如果没有同样可以打电话让宽带运营商给远程修改光猫的IPv6/IPv4双栈桥接。据了解目前很多运行商已经在光猫下发配置的之后已经默认开启了IPv6/IPv4双栈配置。三、RouterOS IPv6开启RouterOS(ROS)默认IPv6默认是关闭的,需要手动开启。System-Packages找到ipv6点击Enable开启。开启后左侧菜单就可以看到IPv6选项了。在IPv6-Settings配置取消"Disable IPv6"设置:四、RouterOS IPv6/IPv4双栈配1、配置文件开启IPv6使用在PPP的Profiles默认配置文件中需要强制使用IPv6选项,才能正常拨号获得IPv6的地址。2、PPPoe双栈拨号之后在PPP-Interface添加PPPoE客户端正常IPv4拨号。IPv4的上网配置将不在此过多的描述,因为已有太多教程可以帮到大家了,本文重点还是继续完善IPv6的设置。同时在IPv6-DHCP Client以IPv6的网口继续获取64前缀IPv6地址,当Status显示Bound说明获取正常。3、双栈DNS配置同时IP-DNS下检查是否正常获取上游DNS地址,如果正常说明IPv6已经正常拨号。注意如果不希望添加运营商的DNS和默认路由设置的话,请勾选掉Use Peer DNS和Add Default Route,可手动配置。提供参考的公共DNS IPv4&IPv6地址配置使用: DNS类型 阿里云 AliYun 腾讯云 DNSPod IPv6地址 2400:3200::1 2402:4e00:: 2400:3200:baba::1 IPv4地址 223.5.5.5 119.29.29.29 223.6.6.6 DoH / Dot dns.alidns.com dot.pub 1.12.12.12 120.53.53.53 4、IPv6 ND配置为了让局域网能够正常获得IPv6地址和上网。继续完善局域网网桥ND配置:5、IPv6网桥地址配置同时给Bridge1网桥分配一个IPv6地址,先按::/64填写,等待几秒,Bridge1网桥自动获得IPv6公网地址(红色变黑色)6、IPV6 DHCP服务器配置IPv6-DHCP Server 添加一个可以分配给网桥下局域网IPv6地址服务器:四、终端IPV6配置验证1、开启IPv6协议Windows要想获得IPv6地址并正常上网,需要再本地以太网网络适配器中打开IPV6协议。2、验证IPv6网络验证一下IPv6配置是否正常上网,可以通过以下两个站点:Test your IPv6 (验证IPv6配置)https://www.test-ipv6.com/ipw.cn (显示本地IPv6公网地址)https://6.ipw.cn/3、配置本地IPv4优先Windows下如果同时开启IPv6和IPv4协议联网,系统默认会优先IPv6,因此为了获得更稳定网络体验,建议设置IPv4优先:///降低IPv6优先级,IPv4优先 netsh interface ipv6 set prefixpolicy ::ffff:0:0/96 100 4///查询网络优先级 netsh interface ipv6 show prefixpolicies///IPv6优先级恢复 netsh interface ipv6 reset
Mikrotik RouterOS IPv6/IPv4双栈配置 前言IPv6:IPV6的提出最初是因为随着互联网的迅速发展,IPv4定义的有限地址空间将被耗尽,而地址空间的不足必将妨碍互联网的进一步发展。为了扩大地址空间,拟通过IPv6以重新定义地址空间。IPv6采用128位地址长度,几乎可以不受限制地提供地址。IPv4:IP协议的第4版本,IPV4为因特网上现行的最重要最基本的协议。IPv4采用32位地址长度,只有大约43亿个地址,目前已经面临分配枯竭。双栈(Dual-stack):双栈技术IPv4和IPv6共存运行在同一个网络一、准备工作RouterOS(ROS)是支持IPv6和IPv4双栈协议的配置的软路由系统。要想配置IPv4和IPv6双栈主要准备工作还是要当地ISP运行商支持。目前三大运营商都已经全部部署了IPv6,所有如果没有IPv6的小伙伴们可以咨询运行商提供。二、光猫IPv6/IPv4双栈配置为了实现RouterOS(ROS)是支持IPv6和IPv4双栈拨号,首先要在光猫上配置IPv6\IPv4双栈设置,当然前提是有光猫的超密才能修改,如果没有同样可以打电话让宽带运营商给远程修改光猫的IPv6/IPv4双栈桥接。据了解目前很多运行商已经在光猫下发配置的之后已经默认开启了IPv6/IPv4双栈配置。三、RouterOS IPv6开启RouterOS(ROS)默认IPv6默认是关闭的,需要手动开启。System-Packages找到ipv6点击Enable开启。开启后左侧菜单就可以看到IPv6选项了。在IPv6-Settings配置取消"Disable IPv6"设置:四、RouterOS IPv6/IPv4双栈配1、配置文件开启IPv6使用在PPP的Profiles默认配置文件中需要强制使用IPv6选项,才能正常拨号获得IPv6的地址。2、PPPoe双栈拨号之后在PPP-Interface添加PPPoE客户端正常IPv4拨号。IPv4的上网配置将不在此过多的描述,因为已有太多教程可以帮到大家了,本文重点还是继续完善IPv6的设置。同时在IPv6-DHCP Client以IPv6的网口继续获取64前缀IPv6地址,当Status显示Bound说明获取正常。3、双栈DNS配置同时IP-DNS下检查是否正常获取上游DNS地址,如果正常说明IPv6已经正常拨号。注意如果不希望添加运营商的DNS和默认路由设置的话,请勾选掉Use Peer DNS和Add Default Route,可手动配置。提供参考的公共DNS IPv4&IPv6地址配置使用: DNS类型 阿里云 AliYun 腾讯云 DNSPod IPv6地址 2400:3200::1 2402:4e00:: 2400:3200:baba::1 IPv4地址 223.5.5.5 119.29.29.29 223.6.6.6 DoH / Dot dns.alidns.com dot.pub 1.12.12.12 120.53.53.53 4、IPv6 ND配置为了让局域网能够正常获得IPv6地址和上网。继续完善局域网网桥ND配置:5、IPv6网桥地址配置同时给Bridge1网桥分配一个IPv6地址,先按::/64填写,等待几秒,Bridge1网桥自动获得IPv6公网地址(红色变黑色)6、IPV6 DHCP服务器配置IPv6-DHCP Server 添加一个可以分配给网桥下局域网IPv6地址服务器:四、终端IPV6配置验证1、开启IPv6协议Windows要想获得IPv6地址并正常上网,需要再本地以太网网络适配器中打开IPV6协议。2、验证IPv6网络验证一下IPv6配置是否正常上网,可以通过以下两个站点:Test your IPv6 (验证IPv6配置)https://www.test-ipv6.com/ipw.cn (显示本地IPv6公网地址)https://6.ipw.cn/3、配置本地IPv4优先Windows下如果同时开启IPv6和IPv4协议联网,系统默认会优先IPv6,因此为了获得更稳定网络体验,建议设置IPv4优先:///降低IPv6优先级,IPv4优先 netsh interface ipv6 set prefixpolicy ::ffff:0:0/96 100 4///查询网络优先级 netsh interface ipv6 show prefixpolicies///IPv6优先级恢复 netsh interface ipv6 reset -
 Mikrotik RouterOS 的防火墙规则脚本 写在前面:以下是给RB5009UG添加的防火墙规则,interface list member中的interface是按我自己家里路由器的接口名称,如要套用,请按实际接口名称修改!一、先配置接口列表/interface list add comment=defconf name=WAN add comment=defconf name=LAN/interface list member add interface=HOME list=LAN add interface=PPPoE list=WAN add interface=CTNET list=WAN二、配置IPv4 防火墙规则/ip firewall filter add action=accept chain=input comment="accept ping" protocol=icmp add action=accept chain=input comment="accept established,related,untracked" connection-state=established,related,untracked/ip firewall filter add action=drop chain=input comment="drop invalid" connection-state=invalid add action=drop chain=input comment="drop all from WAN" in-interface-list=WAN disabled=yes add action=fasttrack-connection chain=forward comment="defconf: fasttrack" connection-state=established,related add action=accept chain=forward comment="accept established,related, untracked" connection-state=established,related,untracked add action=drop chain=forward comment="drop invalid" connection-state=invalid add action=drop chain=forward comment="drop all from WAN not DSTNATed" connection-nat-state=!dstnat connection-state=new in-interface-list=WAN三、防止端口扫描/ip firewall filter add chain=input protocol=tcp psd=21,3s,3,1 action=add-src-to-address-list address-list="port scanners" address-list-timeout=14d comment="Port scanners to list" disabled=no add chain=input protocol=tcp tcp-flags=fin,!syn,!rst,!psh,!ack,!urg action=add-src-to-address-list address-list="port scanners" address-list-timeout=14d comment="NMAP FIN Stealth scan" add chain=input protocol=tcp tcp-flags=fin,syn action=add-src-to-address-list address-list="port scanners" address-list-timeout=14d comment="SYN/FIN scan" add chain=input protocol=tcp tcp-flags=syn,rst action=add-src-to-address-list address-list="port scanners" address-list-timeout=14d comment="SYN/RST scan" add chain=input protocol=tcp tcp-flags=fin,psh,urg,!syn,!rst,!ack action=add-src-to-address-list address-list="port scanners" address-list-timeout=14d comment="FIN/PSH/URG scan" add chain=input protocol=tcp tcp-flags=fin,syn,rst,psh,ack,urg action=add-src-to-address-list address-list="port scanners" address-list-timeout=14d comment="ALL/ALL scan" add chain=input protocol=tcp tcp-flags=!fin,!syn,!rst,!psh,!ack,!urg action=add-src-to-address-list address-list="port scanners" address-list-timeout=14d comment="NMAP NULL scan" add chain=input src-address-list="port scanners" action=drop comment="dropping port scanners" disabled=no四、配置IPv6 防火墙规则,如果有使用ipv6的ipv6 firewall address-list add address=::/128 comment="defconf: unspecified address" list=bad_ipv6 add address=::1/128 comment="defconf: lo" list=bad_ipv6 add address=fec0::/10 comment="defconf: site-local" list=bad_ipv6 add address=::ffff:0.0.0.0/96 comment="defconf: ipv4-mapped" list=bad_ipv6 add address=::/96 comment="defconf: ipv4 compat" list=bad_ipv6 add address=100::/64 comment="defconf: discard only " list=bad_ipv6 add address=2001:db8::/32 comment="defconf: documentation" list=bad_ipv6 add address=2001:10::/28 comment="defconf: ORCHID" list=bad_ipv6 add address=3ffe::/16 comment="defconf: 6bone" list=bad_ipv6 add address=::224.0.0.0/100 comment="defconf: other" list=bad_ipv6 add address=::127.0.0.0/104 comment="defconf: other" list=bad_ipv6 add address=::/104 comment="defconf: other" list=bad_ipv6 add address=::255.0.0.0/104 comment="defconf: other" list=bad_ipv6/ipv6 firewall filter add action=accept chain=input comment="defconf: accept established,related,untracked" connection-state=established,related,untracked add action=drop chain=input comment="defconf: drop invalid" connection-state=invalid add action=accept chain=input comment="defconf: accept ICMPv6" protocol=icmpv6 add action=accept chain=input comment="defconf: accept UDP traceroute" port=33434-33534 protocol=udp add action=accept chain=input comment="defconf: accept DHCPv6-Client prefix delegation." dst-port=546 protocol=udp src-address=fe80::/16 add action=accept chain=input comment="defconf: accept IKE" dst-port=500,4500 protocol=udp add action=accept chain=input comment="defconf: accept ipsec AH" protocol=ipsec-ah add action=accept chain=input comment="defconf: accept ipsec ESP" protocol=ipsec-esp add action=accept chain=input comment="defconf: accept all that matches ipsec policy" ipsec-policy=in,ipsec add action=drop chain=input comment="defconf: drop everything else not coming from LAN" in-interface-list=!LAN add action=accept chain=forward comment="defconf: accept established,related,untracked" connection-state=established,related,untracked add action=drop chain=forward comment="defconf: drop invalid" connection-state=invalid add action=drop chain=forward comment="defconf: drop packets with bad src ipv6" src-address-list=bad_ipv6 add action=drop chain=forward comment="defconf: drop packets with bad dst ipv6" dst-address-list=bad_ipv6 add action=drop chain=forward comment="defconf: rfc4890 drop hop-limit=1" hop-limit=equal:1 protocol=icmpv6 add action=accept chain=forward comment="defconf: accept ICMPv6" protocol=icmpv6 add action=accept chain=forward comment="defconf: accept HIP" protocol=139 add action=accept chain=forward comment="defconf: accept IKE" dst-port=500,4500 protocol=udp add action=accept chain=forward comment="defconf: accept ipsec AH" protocol=ipsec-ah add action=accept chain=forward comment="defconf: accept ipsec ESP" protocol=ipsec-esp add action=accept chain=forward comment="defconf: accept all that matches ipsec policy" ipsec-policy=in,ipsec add action=drop chain=forward comment="defconf: drop everything else not coming from LAN" in-interface-list=!LAN
Mikrotik RouterOS 的防火墙规则脚本 写在前面:以下是给RB5009UG添加的防火墙规则,interface list member中的interface是按我自己家里路由器的接口名称,如要套用,请按实际接口名称修改!一、先配置接口列表/interface list add comment=defconf name=WAN add comment=defconf name=LAN/interface list member add interface=HOME list=LAN add interface=PPPoE list=WAN add interface=CTNET list=WAN二、配置IPv4 防火墙规则/ip firewall filter add action=accept chain=input comment="accept ping" protocol=icmp add action=accept chain=input comment="accept established,related,untracked" connection-state=established,related,untracked/ip firewall filter add action=drop chain=input comment="drop invalid" connection-state=invalid add action=drop chain=input comment="drop all from WAN" in-interface-list=WAN disabled=yes add action=fasttrack-connection chain=forward comment="defconf: fasttrack" connection-state=established,related add action=accept chain=forward comment="accept established,related, untracked" connection-state=established,related,untracked add action=drop chain=forward comment="drop invalid" connection-state=invalid add action=drop chain=forward comment="drop all from WAN not DSTNATed" connection-nat-state=!dstnat connection-state=new in-interface-list=WAN三、防止端口扫描/ip firewall filter add chain=input protocol=tcp psd=21,3s,3,1 action=add-src-to-address-list address-list="port scanners" address-list-timeout=14d comment="Port scanners to list" disabled=no add chain=input protocol=tcp tcp-flags=fin,!syn,!rst,!psh,!ack,!urg action=add-src-to-address-list address-list="port scanners" address-list-timeout=14d comment="NMAP FIN Stealth scan" add chain=input protocol=tcp tcp-flags=fin,syn action=add-src-to-address-list address-list="port scanners" address-list-timeout=14d comment="SYN/FIN scan" add chain=input protocol=tcp tcp-flags=syn,rst action=add-src-to-address-list address-list="port scanners" address-list-timeout=14d comment="SYN/RST scan" add chain=input protocol=tcp tcp-flags=fin,psh,urg,!syn,!rst,!ack action=add-src-to-address-list address-list="port scanners" address-list-timeout=14d comment="FIN/PSH/URG scan" add chain=input protocol=tcp tcp-flags=fin,syn,rst,psh,ack,urg action=add-src-to-address-list address-list="port scanners" address-list-timeout=14d comment="ALL/ALL scan" add chain=input protocol=tcp tcp-flags=!fin,!syn,!rst,!psh,!ack,!urg action=add-src-to-address-list address-list="port scanners" address-list-timeout=14d comment="NMAP NULL scan" add chain=input src-address-list="port scanners" action=drop comment="dropping port scanners" disabled=no四、配置IPv6 防火墙规则,如果有使用ipv6的ipv6 firewall address-list add address=::/128 comment="defconf: unspecified address" list=bad_ipv6 add address=::1/128 comment="defconf: lo" list=bad_ipv6 add address=fec0::/10 comment="defconf: site-local" list=bad_ipv6 add address=::ffff:0.0.0.0/96 comment="defconf: ipv4-mapped" list=bad_ipv6 add address=::/96 comment="defconf: ipv4 compat" list=bad_ipv6 add address=100::/64 comment="defconf: discard only " list=bad_ipv6 add address=2001:db8::/32 comment="defconf: documentation" list=bad_ipv6 add address=2001:10::/28 comment="defconf: ORCHID" list=bad_ipv6 add address=3ffe::/16 comment="defconf: 6bone" list=bad_ipv6 add address=::224.0.0.0/100 comment="defconf: other" list=bad_ipv6 add address=::127.0.0.0/104 comment="defconf: other" list=bad_ipv6 add address=::/104 comment="defconf: other" list=bad_ipv6 add address=::255.0.0.0/104 comment="defconf: other" list=bad_ipv6/ipv6 firewall filter add action=accept chain=input comment="defconf: accept established,related,untracked" connection-state=established,related,untracked add action=drop chain=input comment="defconf: drop invalid" connection-state=invalid add action=accept chain=input comment="defconf: accept ICMPv6" protocol=icmpv6 add action=accept chain=input comment="defconf: accept UDP traceroute" port=33434-33534 protocol=udp add action=accept chain=input comment="defconf: accept DHCPv6-Client prefix delegation." dst-port=546 protocol=udp src-address=fe80::/16 add action=accept chain=input comment="defconf: accept IKE" dst-port=500,4500 protocol=udp add action=accept chain=input comment="defconf: accept ipsec AH" protocol=ipsec-ah add action=accept chain=input comment="defconf: accept ipsec ESP" protocol=ipsec-esp add action=accept chain=input comment="defconf: accept all that matches ipsec policy" ipsec-policy=in,ipsec add action=drop chain=input comment="defconf: drop everything else not coming from LAN" in-interface-list=!LAN add action=accept chain=forward comment="defconf: accept established,related,untracked" connection-state=established,related,untracked add action=drop chain=forward comment="defconf: drop invalid" connection-state=invalid add action=drop chain=forward comment="defconf: drop packets with bad src ipv6" src-address-list=bad_ipv6 add action=drop chain=forward comment="defconf: drop packets with bad dst ipv6" dst-address-list=bad_ipv6 add action=drop chain=forward comment="defconf: rfc4890 drop hop-limit=1" hop-limit=equal:1 protocol=icmpv6 add action=accept chain=forward comment="defconf: accept ICMPv6" protocol=icmpv6 add action=accept chain=forward comment="defconf: accept HIP" protocol=139 add action=accept chain=forward comment="defconf: accept IKE" dst-port=500,4500 protocol=udp add action=accept chain=forward comment="defconf: accept ipsec AH" protocol=ipsec-ah add action=accept chain=forward comment="defconf: accept ipsec ESP" protocol=ipsec-esp add action=accept chain=forward comment="defconf: accept all that matches ipsec policy" ipsec-policy=in,ipsec add action=drop chain=forward comment="defconf: drop everything else not coming from LAN" in-interface-list=!LAN